1. Types of Users
Bitcoin makes the distinction of 4 key functionalities that every node in the network is a combination of:
- Wallets: management of keys and addresses
- Mining: the voting process which expends computational power
- Full Blockchain : a copy of the full Bitcoin blockchain
- Routing: software that allows you to talk to other Bitcoin nodes
We can make powerful generalizations using these 4 key characteristics, however there exist other distinctions between users too.

2. Wallets
The primary function of Bitcoin wallets is to keep track of your identity. In Bitcoin, a private key gives you a claim to your virtual identity; it unlocks your virtual identity and gives you access to your Bitcoin address. Wallets primarily store your private kesy, but most wallet softwares also generate public/private keys with each new transaction and track your transactions. Unlike the physical wallets we use for money, Bitcoin wallets do not store physical bitcoins. They're simply impossible to store. Hence, control over private key is essentially control over identity and bitcoins.
There are two types of Bitcoin wallets: hot wallets (Mycelium, AirBitz, Webapp, Mobile App, etc) are connected at some point to the internet, while cold wallets (i.e. paper and hardware) are not.
You can find them at Bitcoin ATMs, where you can trade cash for bitcoins. You can also get bitcoins through an exchange, where you can trade between different types of fiat currencies and cryptocurrencies. Centralized exchanges are easy to use and access, but are single points of failure which may be vulnerable to hacks.
Decentralized exchanges conduct trades directly between users by creating proxy tokens and are mostly trustless but may suffer from liquidity problems.
3. Wallet Mechanics
For wallets to successfully keep track of your identity and bitcoin, they must implement mechanisms to verify transactions and keep track of may keys.
When using a wallet software, you do not have to download the full Bitcoin blockchain thanks to Simple Payment Verification (SPV). SPV is a method for verifying it particular transactions (specifically your own transcations) are included in a block without having to download entire blocks. Instead, you can simply ask your neighbors for relevant info about the blocks, though you must trust they will give you legimate data.
To maintain anonymity, it is best practice never to reuse pseudonyms. Bitcoin addresses are cheap to generate, and using a new pseudonym for each transaction makes tracking your activity and discovering your identity much more difficult.
The traditional way to keep track of a large number of keys is through a "Just a Bunch of Keys" (JBOK) wallets: a new key pair is created and backed up for every transaction. However, JBOKs are hard to scale. You can see how exchanges have to deal with thousands of transactions a day for thousands of users would need something more efficient than JBOK wallets.
Hierarchically Deterministic (HD) Wallets overcome this problem by deriving all new keys from an original random seed value. In HD Wallets, anyone controlling the parent key can also generate and control child keys.
4. Mining
Mining in Bitcoin requires miners to verify incoming transactions, create a block, find a valid nonce, broadcast the block, and earn a profit in bitcoins.
Miners are primarily motivated to maintain the network, or execute the Proof-of-Work consensus mechanism and bring new bitcoin into circulation, by earning profit. Miners only earn a profit from mining when the revenues from the block reward and the transaction fees are greater than the fixed and variable costs of mining.
A block reward is a reward that goes to iners whose blocks are included in the longest chain. Bitcoin incentivizes honest mining by rewarding miners in bitcoin. The block reward halves every 210,000 blocks, approximately 2 years, and will fall to 0 once 21 million bitcoins have been mined.
Regardless of the number of bitcoins in circulation, miners will always be rewarded via transaction fees.
The main fixed cost in mining is the hardware that allows users to mine. CPUs, GPUs, FPGAs, and ASICs are all types of hardware that have been used for mining, and each is more computationally powerful than the last. ASIC, which stands for Application Specific Integrated Circuits, are currently capable of omputing 14 trillion hashes per second. They are fully specialized devices that can only do one activity: mine for Bitcoin.
The main variable costs associated with mining are energy and infrastructure costs. Energy costs are further divided into three types: Embodied Energy, to produce hardware; Electricity, to power hardwarel; and Cooling, to maintain hardware.
5. Real World Mining
To get a better sense of how mining looks in real life, here is what a real-world ASIC mining farm in China looks like:

Even with the most impressive technology, it still takes a great amount of time and power to find a block. Mining pools allow miners to join their hash power together so that they will collectively find blocks and collect rewards more often, reducing variance. As a member of a mining pool, your reward is calculated by the number of "shares" you contribute. A share is defined as a nea valid block, used to estimate the mining power you contributes. More shares equals more attempts at finding a valid nonce equals a larger slice of the pie.
The two main payment mechanisms in mining pools are :
- Pay-per-Share: where miners are paid a fixed amount of money for each share, regardless of how much reward the pool makes
- Proportional Schemes, where miners receive a reward proportional to the number of shares submitted before the block was found
Pay-per-Share pools are advantageous to the miner because of guaranteed payouts, but risky for the pool because miners have no incentive to submit valid blocks to the pool. Proportional Schemes are advantageous for the pool because the pool operator only pays out after a block is found, but more risky for the miners due to greater variance of reward.
6. Changing Bitcoin
One of the current challenges of Bitcoin is that mining is tending towards centralization with the development of ASICs, mining pools, and mining farms. ASICs cost a lot of money, which means only those with access to high volums of capital can afford them, thereby concentrating the mining power into the hands of a few. To address this issue, we must develop a tweak to the protocol that reduces centralization but still adheres by the puzzle requirements (quick to verify, adjustable difficulty, and computationally difficult).
We can get around the ASIC domination by creating a memory-hard or memory-bound puzzle, periodically switching mining puzzles, or replacing Proof of Work by Proof of Useful Work.
While ASIC resistance may decentralize mining and make it a more democratic process, achieving ASIC resistance may also cause disruptions to the mining community that would undermine the network.
Real changes are implemented in Bitcoin via hard or soft forks. Hard forks result from a new protocol that does things not allowed in the old protocol. In a soft fork, the rules of the protocol are only restrained. A soft fork is backwards compatible but not forwards compatible.
Hard Fork:
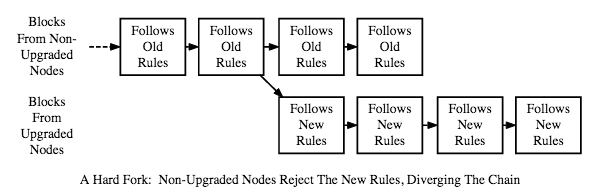
Soft Fork:
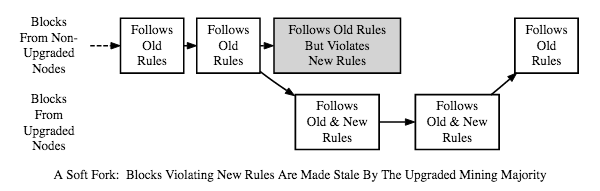
In Bitcoin, changes to the protocol come in the form of BIPs, or Bitcoin Improvement Proposals. These can be changes in the network protocol, block or transaction validation, or anything affecting interoperability. There are three main kinds of BIPS: standard, informational, process.
이 글은 edX의 Bitcoin and Cryptocurrencies 강의 자료를 참고하여 정리한 글입니다.
'0 > blockchain' 카테고리의 다른 글
| Ethereum Scaling (0) | 2021.11.19 |
|---|---|
| 재밌는 스마트 컨트랙트, NFT 튜토리얼 (0) | 2021.10.29 |
| Bitcoin and Cryptocurrencies Week 4 (Mining) (1) (0) | 2019.05.12 |
| Bitcoin and Cryptocurrencies Week 3 (Bitcoin Mechanics & Optimizations) (3) (0) | 2019.05.12 |
| Bitcoin and Cryptocurrencies Week 3 (Bitcoin Mechanics & Optimizations) (2) (0) | 2019.05.12 |

